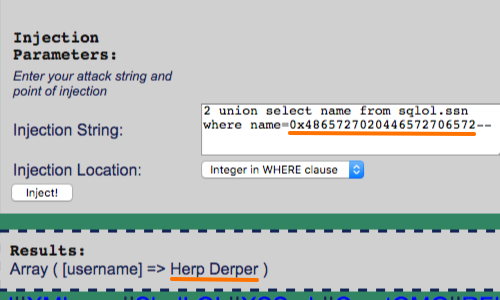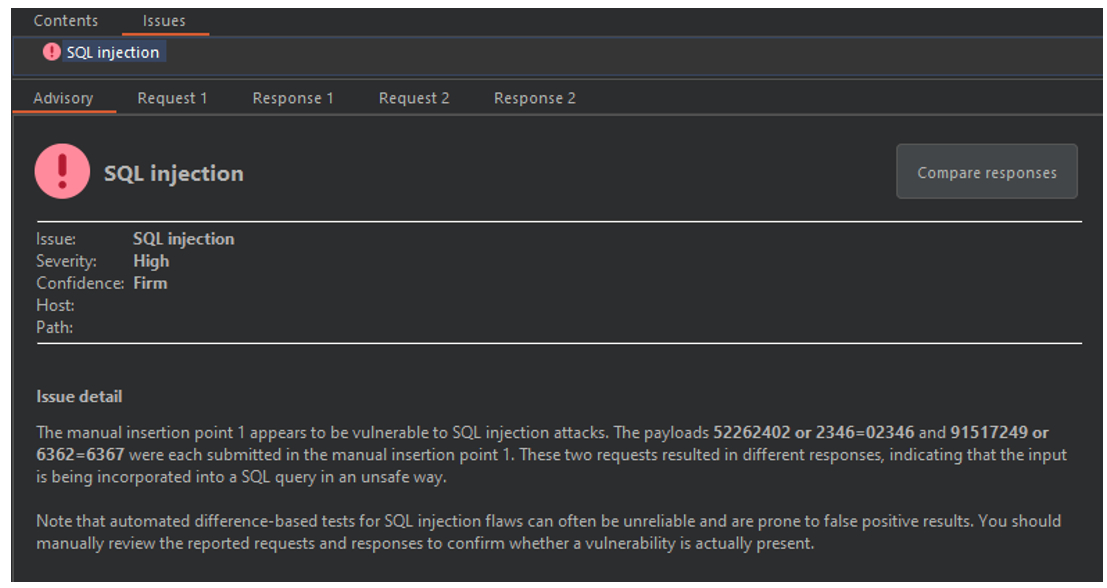
Jason Haddix on Twitter: "My whole set of SQL Injection attack and defense resources and cheat sheets here - https://t.co/8t8GQqXhqJ http://t.co/a31XH6pbZp" / Twitter
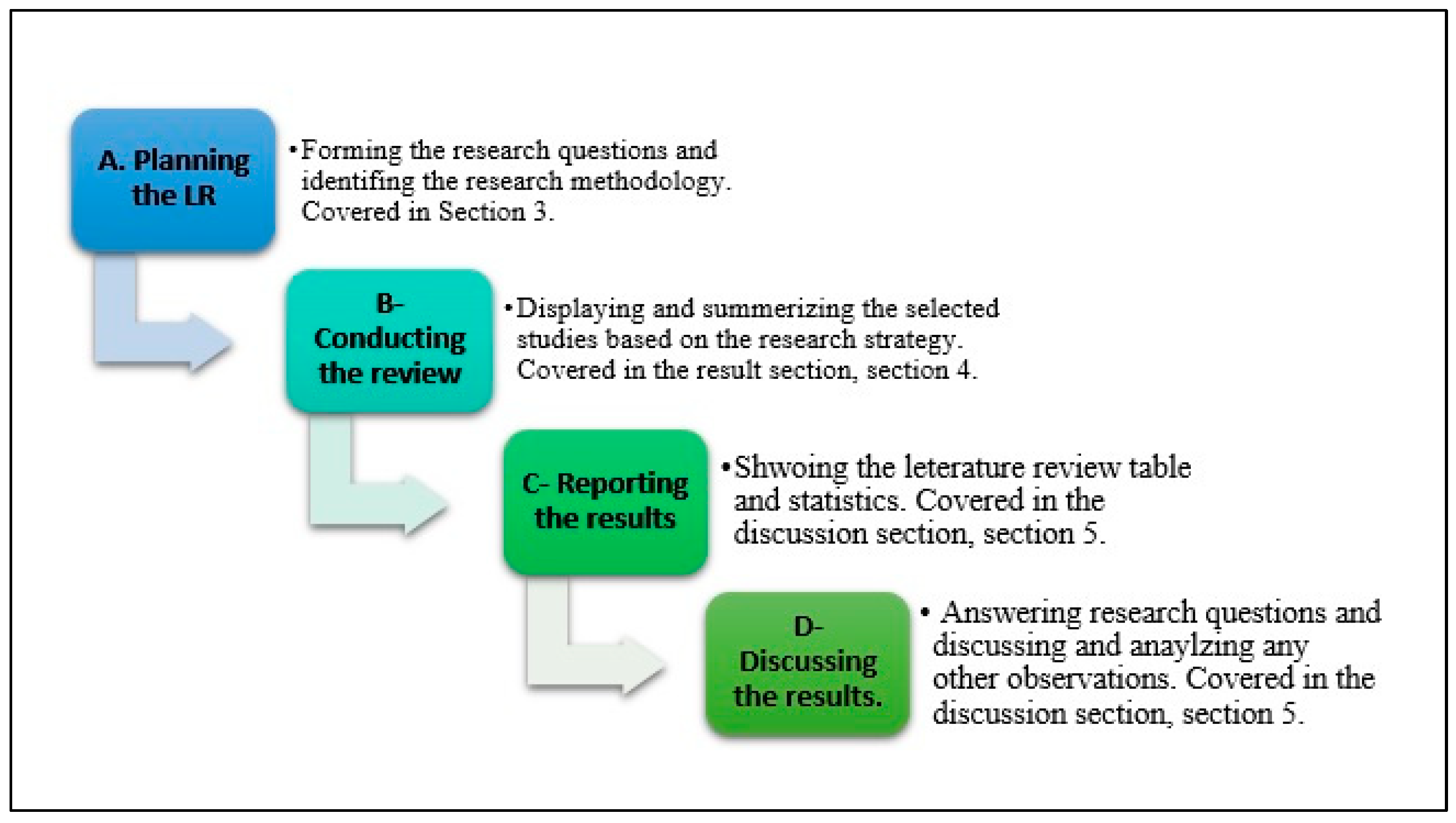
JCP | Free Full-Text | Detection of SQL Injection Attack Using Machine Learning Techniques: A Systematic Literature Review